The Invisible Risks of Insecure Chinese Surveillance Cameras

This article is based on research conducted for an academic paper titled ‘Cyber Vulnerabilities and Technical Regulation of China-made IoT Surveillance Cameras in Australia’ originally published on February 24, 2025, by SSRN.
Smart devices that connect to the internet are all around us. A 2023 survey from Australia found that the average Australian household has 24 internet-connected devices, which include phones, smart household devices like fridges and espresso machines, and home surveillance cameras, with the latter being particularly insecure. Although security cameras make up only 5 percent of Enterprise Internet of Things (IoT) devices, they account for 33 percent of all security issues. Two Chinese suppliers – Hikvision and Dahua – dominate international markets due to their competitive prices and product features. Our recent study shows that both of these brands are easily exploitable and slow to repair reported vulnerabilities.
In addition to the technical issues, the geopolitical misalignment between China and European countries adds urgency to the need to address these national security risks. This is because large Chinese manufacturers are supported by the Chinese government, and emergent evidence shows that 80 percent of sanctions circumventions against Russia are facilitated by China, with 80 percent of dual-use goods routed through China.
These vulnerabilities are a concern for individuals, enterprises, and government entities alike. Evidence of illegal camera hacking that we have available indicates that individuals are often targeted for personal or for-profit streaming of camera footage. Moreover, when surveillance cameras are installed in critical locations, such as federal or state government buildings, the likelihood of that location becoming a surveillance target increases.
Video showing how a camera can be hacked in 11 seconds. Source: BBC
Types of Attacks Enabled by Insecure Cameras
There are three types of risks associated with surveillance cameras: targeted surveillance of individuals, national security risks, and exploitation of network security vulnerabilities. Unwanted individual surveillance most often occurs in the form of covert or overt hacking of individual cameras. Hacked cameras have been used to record and sell child exploitation material, as well as video recordings from gynecologists’ offices and locker rooms. Individual users should connect cameras to their own private networks and monitor the number of connected devices.
Once considered hypothetical, national security risks posed by surveillance cameras have become real since the start of the Ukraine-Russia war in 2022. In 2023, the Ukrainian government added Hikvision and Dahua to its list of international sponsors of war. Insecure cameras have thus become part of the war in Ukraine, with targeted campaigns seeking system access to monitor aid efforts. Several European national cyber authorities have privately voiced concerns about potential backdoor code in Chinese-made cameras.
Unsecured cameras have also been exploited in botnets to launch large-scale cyberattacks. A prominent example is the Mirai botnet, which in 2016 hijacked hundreds of thousands of internet-connected devices, including surveillance cameras, to execute one of the largest Distributed Denial-of-Service (DDoS) attacks in history – crippling major websites like Twitter, Netflix, and Reddit. Variants of Mirai and similar malware continue to target vulnerable surveillance systems, enabling attackers to disrupt infrastructure, financial services, and government operations.
Case Studies of Confirmed Tracking
Numerous cases of surveillance camera exploitation have made it clear that these risks are well-documented. A few particularly alarming incidents highlight how these devices can be weaponized for foreign interference and surveillance of vulnerable populations.
In 2018, the French newspaper Le Monde reported that the entire contents of the African Union’s information servers – located at its headquarters in Ethiopia’s capital city Addis Ababa – were being transferred to China every night. This breach was made possible because the building had been handed over to the African Union as a turnkey gift from China. Later reporting in 2020 confirmed the security breach and attributed it to a Chinese hacking group nicknamed “Bronze President.”
In 2023, cybersecurity firm IPVM revealed that criminals were disturbingly exploiting vulnerabilities in Hikvision cameras to stream and sell illicit content, including child exploitation material, via public Telegram channels. Before being taken down, the content posted on Telegram channels was advertised as showing both children and adults, with one channel selling feeds by hacked cameras for as little as $3 to $6 each.
Regulatory Responses and Mitigation Efforts
Regulating or securing millions of cameras worldwide is no easy feat. Steps taken by different countries include bans, sales restrictions, and stricter cybersecurity requirements. Some countries in Europe and elsewhere have issued blanket bans or restrictions on purchasing Chinese cameras, primarily citing national security concerns.
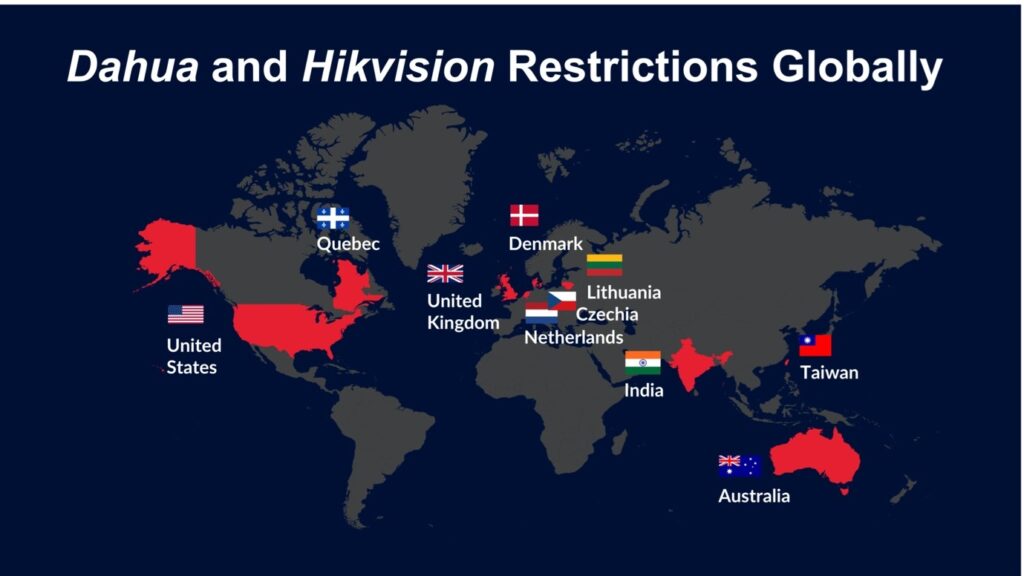
Map of countries with regulations on surveillance cameras
At the same time, the European Union has focused on establishing technical cybersecurity requirements for products with a digital component, including cameras. The EU’s Cyber Resilience Act, passed in 2024 and due to come into effect in 2027, introduces strict cybersecurity rules for smart devices like IP cameras. It requires manufacturers to design these products with security in mind from the start, fix vulnerabilities quickly, and provide regular security updates throughout the product’s life cycle. Companies will also have to clearly inform users about safe usage and report any major security issues.
Another example is India’s Electronics and Information Technology Goods Order, effective since April 2025, which focuses on controlling the cybersecurity of cameras at the import stage. India’s new security regulations mandate that CCTV camera manufacturers submit their devices’ hardware, software, and source code for evaluation in government laboratories before they can be sold in the country.
Although cameras are devices that were created to enhance environmental security, they have now introduced new security concerns due to their technical shortcomings and social applications. Establishing robust security standards is essential for IP cameras used in government buildings, business premises, and individual homes. Against this background, the EU’s Cyber Resilience Act that will place greater responsibility on manufacturers and distributors to produce and supply more secure devices, is a step in the right direction.
Written by
Ausma Bernot
Dr Ausma Bernot is a Lecturer in Criminology at the School of Criminology and Criminal Justice at Griffith University. Her research focuses on the intersection of technology and crime, with a particular focus on surveillance and technology governance.


